LOIC (Low Orbit Ion Cannon) � DOS attacking tool

Low Orbit Ion Cannon (LOIC) is an open source network stress testing and denial-of-service attack application, written in C#. LOIC was initially developed by Praetox Technologies, but was later released into the public domain, and now is hosted on several open source platforms.
The software has inspired the creation of an independent JavaScript version called JS LOIC, as well as LOIC-derived web version called Low Orbit Web Cannon. These enable a DoS from a web browser.
LOIC basically turns your computer’s network connection into a firehose of garbage requests, directed towards a target web server. On its own, one computer rarely generates enough TCP, UDP, or HTTP requests at once to overwhelm a web servergarbage requests can easily ignored while legit requests for web pages are responded to as normal.
But when thousands of users run LOIC at once, the wave of requests become overwhelming, often shutting a web server (or one of its connected machines, like a database server) down completely, or preventing legitimate requests from being answered.
Tutorial :
1. Download the software and execute it. lets describe it with a screenshot!
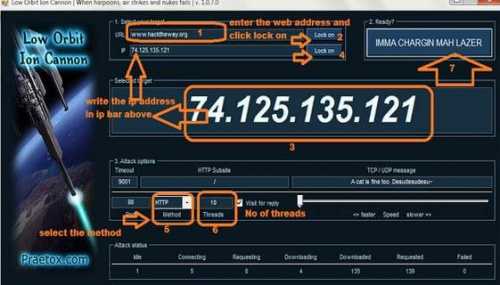
2. Enter the URL which u wanna attack and click on Lock On.
3.The ip address of that very site will get displayed in the “Selected target” caption. Write this ip address in ip bar as shown above and click Lock On.
4. Select the method and number of threads.
5. Click on IMMA CHARGIN MAH LAZER…
Cheers You’re done……….
http://www.mediafire.com/?ctg8c3186mimqx7
we are anonymous
Fuck that! Just bring it down to backtrack/kali…. Unless you have a mass of attackers using LOIC not much is going to happen and firewalls/tunnels that can filter your attacks. You’re better off building your own attack and actually learning something without using software.
But– Note the speed of a 3G cell phone ;) if you get the LOIC app for android you can take down a single users pc (I don’t know about a server that’s been put together well and prepared for these attacks though) from approximately 1958 miles within an estimation of 2-4 minutes by yourself. I know this from experience.
Here’s the link from android (free @ Google playstore): https://play.google.com/store/apps/details?id=genius.mohammad.loic&hl=en
Use HTTP for the reasons that the packet size can get pretty hefty and run around 600-750 threads no more using the fastest setting (slider all the way to the left). The app will more than likely crash if you exceed 600-750. When I used it was stable around there but any higher dead. I took a pretty good analysis of these tools too since the whole purpose was to show my friend how to perform a Denial of Service Attack.
But as I said before, what are you really learning from using someone else software? That just makes you a script kiddie. I mean yeah you’re using others software by using software at Linux hacking software, such as metasploit and other tools, but you’re still getting familiar with using command line interface. While you’re at it look into some good proxies and pick up a programming language/ Here’s another glass of water http://www.codecademy.com/ . Python is a pretty easy start an compatible with most Linux distributions. Step1: Create your script… Step 2: Put it in an organized folder Step 3: Run it.. example>
cd /python_scripts/hacks/
[ENTER]
python myhackingscript.py
[ENTER]
Boom!!! :P
Anywho' I’m going on lol but just saying I’d rather use windows to perform a ddos attack on command shell than LOIC. Just because hacking with GUI requires no skill or knowledge whatsoever! If you want to become a successful hack… Become an information junky don’t half fast it that’s how you get caught. How do you know you can trust someone else’s code and that they aren’t logging in your computer and on their servers, every time you use their software? Think about it….
Not saying LOIC isn’t a clever tool but, it’s kind of obsolete, weak, and noobish….
Here’s pretty much speech of every Denial of Service attack possible @ Defcon ( <3 ), and has some stuff about anonymous and Lulzsec if you’re interested. Pretty much teaches how and what’s going on here.
Anyways!
Cheers!!!
11 years ago
1
Nice post mate (:
Im no fan of LOIC!
I’m actually still a noob myself.
I use Kali Linux because i love Linux and because i love the tools they provide, helps me on the way!
i’m no programmer so im grateful for all the programmers out there, im kind of a script kiddie yes, but why make Kali linux if not to be used by us :b
I never act as if im better than anyone else because that wont help me nor the person im helping (:
so thanks for sharing, i’ll say ( :/ to LOIC, :) to the POST ) !
Have fun !
Ha ha thanks for the reply and Not saying it’s a bad tool just very obsolete and not much to learn from pushing a couple buttons. lol I mean it serves its purpose of gathering a couple hundred people who hate Scientology together and flooding their networks with data, yeah, but to call yourself a hacker you have to have a little more up your sleeve than just LOIC… cause I mean when your attack fails there’s a million other options but, unless you have a back up plan on what those options are and some knowledge it’s no use. So if you know other types of denial of service attacks then yeah go for it! Serves your purpose as an activist/hacktivist. But hacking usually refers to accessing data/information in unconventional ways. So I don’t get that out of a denial of service of service attack. Plus DOS/DDOS attacks tend to be risky y ‘know. Your ip info is present, information of your system being distributed back and forth, creating somewhat of a connection I guess in a weird way. Just it’s simple to track…. If you want to take down a companies website, play like a ransom. Use your crafty/creative hacker skills to gain access to the server, create a backdoor, make a back up of the the site and databases, once all that good kidnapping stuff is down, lock up all connections to the server (again use crafty hacker skills: crash the server, plant a smart virus, redirect, deface, a back door with a shell running, etc.) and finally delete all of your logs. Security precautions and a plan on how to execute your attack should be done before hand though y 'know?! So Idk I think that’s more efficient I guess than a ddos. Spend some extra time and don’t get busted why not lol. I can’t really think of anything because, I do not have any big companies I’m after right now ha ha!
Now, being a script kiddie and using other line user interface tools? I wouldn’t really say that’s being a script kiddie. I mean depends on the extent you go to… Like if your using something that requires a lot of custom input and data that you’re retrieving on your own such as, net work maps, port scanning, database injection scanning, etc. and then inputting it in the software? Then “I” at least wouldn’t say that would be a script kiddie. Other, very “advanced” / egotistical people would beg to differ but y ‘know what… I’m not them! Now if you’re using a lot of button click / gui based stuff that’s like, “Enter Ip address… Okay hacking… loading…. hacked! Would you now like to see their screen? y o n? okay loading screen shot” then yeah I would or if it’s something simple like armitage then yeah…. script kiddie all the way. But, don’t condemn the script kiddies because, they’re learning y 'know and we all start somewhere right?
Picking up Python is fairly easy since it’s plain English but it’s different in a weird way and idk how to explain check it out for yourself. Imagine if command line made a baby with a standard programming language. That’s what you would get I guess :/ there’s so much on codeacademy though seriously check it out. Backtrack was fun and had some cool linux stuff I’m not going into but the consistency with Kali and the stability is excellent unless you’re running from a usb then, the network drivers tend to give out. But that’s also when it was new, I’ll have to check back in, maybe see if KDE is in yet all they had was GNOME last.
Anyways thanks for responding to my post. I was hoping at least somebody would lol
Cheers!
11 years ago
0
Thanks for your big and awesome reply ;) !
This made me think a bit more hehe, i still call myself a script kiddie because im just not that good yet, i now go at a education where when im done i can call myself a Data Technician with the speciality of Infrastructure, i learn a lot about networks and operating systems, but hey there is also some programming of course, im glad to finally join in on an education i like and im happy that i still got this lovely community to fall back to, coes the more i learn from this education the more i can use it in the dark world of hacking, Dark world is depending on what you do, i mostly sit in a dark room with some headphones on if im trying to get access to something gives me a clear mind only focusing on what the hell im doing :b
but i came to this site hoping to learn and so far i learned a lot, even from this reply of yours i learn small things or at least my memory is being refreshed :)
Thanks for the reply mate.
Peace - Th3FjonG
Just on the topic of Script Kiddies, I know I’m new here, but that codeacademy website is great! I’m doing HTML and Javascript, and will be starting PHP when I finish HTML (around 60%). I use the metasploit command interface as I want to see the different options better, and its easier for me to understand (and I can’t afford all this ‘auto select exploit’ stuff on the Web GUI!). But i’m starting off with it, and if yo have any experience with metasploit could you please check my post in the Tools & Utilities forum, i’m sort of stuck with metasploit, and google isn’t going anywhere… Thanks! (Sorry to Mods for deviating…)
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
@MaxLockhart Cheers for that DOS attack presentation on youtube!
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
Haha you’re welcome @loltac you gotta get down to the real business lol
Forwarded to my mate, he loved it as well! ICT teacher wasn’t happy when we were talking about the best way to bring down the school website… Th3J3st3r style with Slowloris/mobile? :) or attempt an Iv6 attack? Unfortunately our school systems aren’t running it… Those evil eyes haha
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
Oh i’m not gonna do one :) the trace of LOIC is so obvious, however you should definitely take a look at what is known on XerXes !
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
Actually don’t underestimate the power of using LOIC with the power of a 4g cell phone. Brought my mates, clear accross the country, internet down in 5 minutes. 2 minutes his connection slowed down, 5 minutes– connections timed out. It was fantastic… via computer though it doesn’t really do anything at all. Using a cell phone be careful though. I have a really shitty android phone so, I could only go up to about 720-1000 or so threads before my the app would crash. Any higher my phone would reset. I still have it installed as a last resort tool y ‘know but I will never use it. As I said I do not care for denial of service attacks.
Also you have to keep in mind. How many servers do they have up? How are they tunneling that traffic. You may want to attack the dns servers instead to keep the server access down all around the world. For Example… nslookup facebook.com
Here in America I get 173.252.xxx.xx but in the UK you may get something entirely different. Who knows? If you look it up for me and post the results here to enlighten me that would be great.
btw Love that meme you have there. Haha it’s hilarious. Anywho, if let’s say we attack a low budget website with only 1 server up then the sites going to drop like a rock. It’s all about the money and resources you have to keep your security. Well except for us hackers who can build our own tools, devices, and set up our own security, test it a shit load of times until it’s perfected and yeah.
@Paulau I can vouch for LOIC, i’ve seen a small website taken down by one person! However, its demanding on the computer and more obvious to see as it sends so pany packets, whereas SlowLoris sends incomplete packets which tie up the port for much longer, reducing strain on the computer… Its also better for phones, they’ve even got an app! Heck…
@MaxLockhart That DoS presentation on youtue you linked summed it up generally…
LOIC = lots of people one site down
Slowloris= one person multiple sites down…
Generally!!!
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
Any advice on where to go for presentations of website takedown? Just presentations or practice websites (like this one!)
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
huh? @loltac
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
Do you mean website deface? @loltac
Well yes, topics like that… Just procrasination like :) but deface/take down/data taking (rfi/lfi/sql)?
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
@aqua-squad I don’t understand you? If you mean will it show a websites IP, yes. If it will take the website down, most of the time no. No point trying to extort google haha.
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
As in a 192… IP address? Hmmm, someone more experienced would need to tell you, but my first thought would be that unless it’s a server no…
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
@FlabbyRabbit @Angellomichel387 …. Is it a server you’re trying to take down, or a computer on the same network as you?
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
Meh, depends how technical you want to get… There are tools that take your individual packets and send them through a network of computers, then onto the server. I know that could be called a bot net, but if it’s a Tor style network, or you hijacked Tor itself then you could make it a DDoS.
“What hackers do is figure out technology and experiment with it in ways many people never imagined.” - A Person Procrastinating by Hacking…
http://sourceforge.net/projects/javaloic/?source=directory
here is a link for the Loic Good luck ;)
@deafrascal Just download the windows version and use it through wine…
@aqua-squad Please open up a new thread for this. Although, I suggest you just check out the guys on HT IRC. I think some of them can help you out!
Don’t post answers on the forums!
Search other forums before making new threads called “help” !
